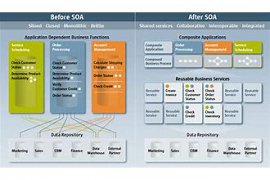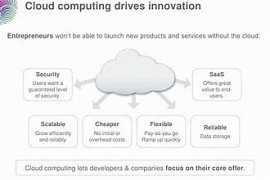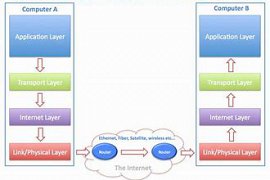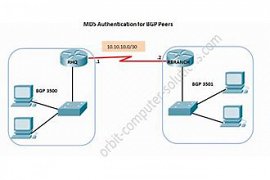
18
Fiber Distributed Data Interface
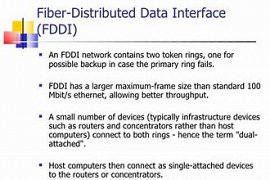
F, de iPhone, with the interface distributor, data networking, fiber optics (briefly: F, Di, IP), a local area network with high speed. that from the layout (topology) of the annular speed of 100 Mbps for the exchange of Information uses. F,, ay of the two rings. so the topology of the annular dual called. In this method, F,, iPhone similar with the standard IEEE802.5 in tokens rims. One of the most important properties of f, your use of the media transfer optical fiber to exchange data. Important advantage of using optical fiber over copper wire protection and security on top of it. because in this medium the electric signal does not exist, to which it hears. In addition, the noise is also on its impact will be.
F,, ay of the two rings, which uses include: ring primary Ring Secondary. Swap the data in the ring in two opposite directions. ring the primary to send the data is used and the ring secondary when the ring primary, sliding, etc. as a backup for it, the ring goes to work. PDF, your allows connection of up to 1000 stations to the ring. meanwhile, can the length of a maximum of 200 km, spread.
the standard F, de iPhone the first time by the American National Standards Institute X3T9.5 in 1980, was then to model the Cross Connection System, Open-was presented. This Institute of writing a new standard, F, IP defined... with the standard of the current American National Standards Institute compliant....