15
Password
passwd the name of a program in most operating systems, Unix and Unix-like by which users can have their passwords changed. Password that the user entered. using a key derivation function for Tangled has been released when this version of UAE are stored. According to the security reasons, the original version of the password will not be stored and only version of UAE are stored. When the user enters the system. password while log in to enter again using the same key derivation function for UAE visit it, and the result of the operation with a version that saved to a. if equal. the user login to the system is reduced.
file /etc/passwd includes information related to the users of the system. In this file, for any new user that define a line be added that each line of the seven fields, of the fields with the character ‘:’ separated.
this field from the following are:
field first: the name of the user, this is the name for the log is used.
field two: this field contains the password of the user. The password for the encryption has been written to be selective.
field three: the UID of the user. In the systems unix-base every user a number of unique.(Something like number, ID cards or student number)
the fourth field is the group identifier. Each user, at least a member of a group and that each group together a number of exclusive.
field V: for this field to another field, is divided into with ‘,’ separated.
field of the first: containing the full name and the real user is (when you send and receive email, the name is displayed.)
field two: room number of the user.
field three: work phone a user
the fourth field is the phone number of the user's home
field V:other information
the sixth field is the full path to the user's home directory.( The home directory where the user has full access to it, and files his personal as much maintenance.)
field seventh: the full path of the Shell (shell) Default User, this field can be written.
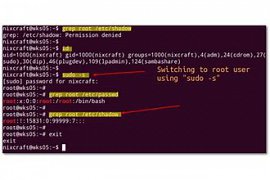
field the second that contains password encryption, the user can empty. In this case, there is no password for the authentication of the user question not be. In the event that this field is empty. some of the programs that the file /etc/passwd to read, etc. might that allow any access to the user." If the field password contains a character ‘x’ (for small). password, the real user in the file /etc/shadow is stored. In this case, the file /etc/shadow must contain a line for this user, otherwise the user name, non-valid to be considered.
if this field contains any other field. with its string, like a password encrypted would be dealt with.
field V by some applications like finger is used.
the sixth field is the represents the home directory of the user. Home directory of the user where when the user to be logged in there are. App login of this field is for the amount of this to the environment variable $HOME.
field, the seventh characteristic of the shell default user. Of course, you can address every other program take the time to write. In this case, program it to when user login will be implemented. If this field is blank, the shell by default, which is usually /bin/sh is for the user are considered.
file /etc/passwd - is a backup of this file....