22
Blind Carbon Copy
Transcript unsuspected that the Bcc know the phrase, it is, and the abbreviation of it is used. Bcc is a method to send email to other people is so that the name of the people who are in the Bcc write from other people\'s hidden remains.
general to send the email in three parts, can email address, the recipient enter:
1) in part \"To\", which the main receiver of the letter.
2) in the episode \"CC\" someone that you want, Plus include the original email you received (a copy of the letter).
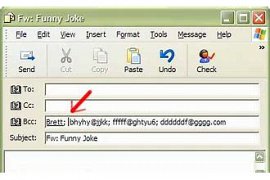
3) in the episode \"BCC\" personal is that without the knowledge of the other recipients (to ,cc), email you receive (i.e., those in to and cc are individual email is in the bcc written will not see).
using BCC, it is possible to keep secret the address of the recipients of an email. will be provided. Unlike the address that is in the field To or CC inserts, and the possibility of viewing them by other recipients, there is the possibility of viewing the address listed in field BCC by other recipients, there will be no (send copy of letter to a third person without the recipient of the initial letter is given.)...
general to send the email in three parts, can email address, the recipient enter:
1) in part \"To\", which the main receiver of the letter.
2) in the episode \"CC\" someone that you want, Plus include the original email you received (a copy of the letter).
3) in the episode \"BCC\" personal is that without the knowledge of the other recipients (to ,cc), email you receive (i.e., those in to and cc are individual email is in the bcc written will not see).
using BCC, it is possible to keep secret the address of the recipients of an email. will be provided. Unlike the address that is in the field To or CC inserts, and the possibility of viewing them by other recipients, there is the possibility of viewing the address listed in field BCC by other recipients, there will be no (send copy of letter to a third person without the recipient of the initial letter is given.)...