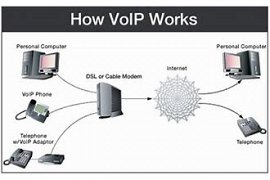
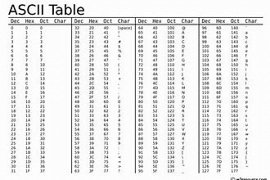
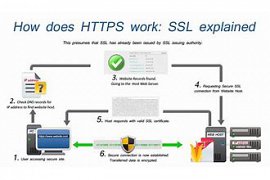
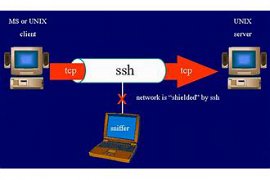
63
Computer Numerical Control
Digital control computer, or CNN to steering the machine tool, and industrial with the use of a computer is said to be.
by CNN can be quickly fragments with the size, exact from metal or wood, right. The Shape of the components of the AGO by a program that in the system (CAM), or by using manually (Manual) produced is determined. Usually for this purpose, frequently, from the standard (EIA-274-D (ISO6983 used that code a (G-Codes) also called, in this standard the files, move the tools, and the performance of the sequential device to specify. On standards, newer devices CNN News ISO 10303 and ISO 14649 file input operations necessary for the production of the workpiece to define the work of each device according to the tools and capabilities of the. path of motion it produces....
by CNN can be quickly fragments with the size, exact from metal or wood, right. The Shape of the components of the AGO by a program that in the system (CAM), or by using manually (Manual) produced is determined. Usually for this purpose, frequently, from the standard (EIA-274-D (ISO6983 used that code a (G-Codes) also called, in this standard the files, move the tools, and the performance of the sequential device to specify. On standards, newer devices CNN News ISO 10303 and ISO 14649 file input operations necessary for the production of the workpiece to define the work of each device according to the tools and capabilities of the. path of motion it produces....